Hi,
Welcome to my blog!
In this post, I will make a write-up of Traverxec, a machine on Hack The Box which just retired. It's my first own box and helped me learn a lot to hack more others. Although it's rating difficulty is easy (and the root owning is definitely easy), the user part may be a little tricky.
I solved this box when I was preparing for OSCP but I finished the Exam a few days ago. Although I rooted 4/5 exam machines, I might have to retake it due to the missing of one screenshot.
Ah, the nmap's report shows that Traverxec has a website that runs on Nostromo 1.9.6. As you know, the Nostromo web server, aka nhttpd, has an unauthenticated remote code execution in all versions before 1.9.7. So, it must be the point to get the initial shell!
If you want to analyze this vulnerability, named CVE-2019-16278, you can read more at my blog post.
In my machine (I use a Kali Linux 2019.4 virtual machine), I run a listener by using nc. After getting the reverse shell, I use Python to spawn a TTY. If you don't have a TTY, many commands like su, sudo,... will not work.
Now, let's dig deeper into the box. The /home directory contains only a folder named david so it must be the user we have to own.
I search in the Nostromo's directory, /var/nostromo, and find some useful information.
First, the file .htpasswd contains username and password hash for HTTP Authentication. I hope that the user david reuses this password for his other accounts so I immediately use john to crack it and find out the password is "Nowonly4me".
Unfortunately, he doesn't (he may be a professional admin ). I tried to switch to david with the command su but it keeps saying "Authentication failure".
A bit stuck, I read the config file nhttpd.conf and the Nostromo's manual again. Oh! There is something I forgot, it's the homedirs. This configuration allows users to access their home directory by an URL with the character "~" like that: http://10.10.10.165/~david/
Although the directory /home/david is not accessible, I can still access the directory /home/david/public_www, which is shown at the configuration homedirs_public. Browsing this directory, I see a backup file named backup-ssh-identity-files.tgz. Maybe it contains the ssh key to access the david account!
Do you remember the password hash in the file .htpasswd which we've just cracked? Using these credentials david / Nowonly4me, I can download the backup file via the browser by access this URL:
http://10.10.10.165/~david/protected-file-area/backup-ssh-identity-files.tgz
Extracting the backup file, I find the private key file which we need. However, it's encrypted by a passphrase so I use john to crack it.
Now, using the passphrase "hunter", I can ssh to the david account and own the user flag.
Inside this file, there is only a command takes my notice:
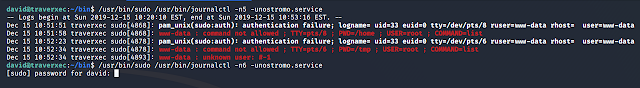
Oh, a command with sudo, it's definitely where to get root! If you know GTFOBins, you may also know that journalctl will invoke the command less and inside the less window, you can spawn a shell. Here comes a trick, if your terminal's width is smaller than the output's longest line, the less window will be held and you can spawn a shell from it. Otherwise, it will return back to the terminal.
Note that you can only use exactly the command "/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service" to run with sudo privilege without a password in this box.
Finally, we just grab the root flag!
If you have any questions, please don't hesitate to ask me on Twitter or leave a comment.
Thank you for reading!
Welcome to my blog!
In this post, I will make a write-up of Traverxec, a machine on Hack The Box which just retired. It's my first own box and helped me learn a lot to hack more others. Although it's rating difficulty is easy (and the root owning is definitely easy), the user part may be a little tricky.
I solved this box when I was preparing for OSCP but I finished the Exam a few days ago. Although I rooted 4/5 exam machines, I might have to retake it due to the missing of one screenshot.
Port enumeration
Ah, the nmap's report shows that Traverxec has a website that runs on Nostromo 1.9.6. As you know, the Nostromo web server, aka nhttpd, has an unauthenticated remote code execution in all versions before 1.9.7. So, it must be the point to get the initial shell!
If you want to analyze this vulnerability, named CVE-2019-16278, you can read more at my blog post.
Own user
I use my Python script of CVE-2019-16278 to make a reverse shell back to my local machine.In my machine (I use a Kali Linux 2019.4 virtual machine), I run a listener by using nc. After getting the reverse shell, I use Python to spawn a TTY. If you don't have a TTY, many commands like su, sudo,... will not work.
Now, let's dig deeper into the box. The /home directory contains only a folder named david so it must be the user we have to own.
I search in the Nostromo's directory, /var/nostromo, and find some useful information.
First, the file .htpasswd contains username and password hash for HTTP Authentication. I hope that the user david reuses this password for his other accounts so I immediately use john to crack it and find out the password is "Nowonly4me".
Unfortunately, he doesn't (he may be a professional admin ). I tried to switch to david with the command su but it keeps saying "Authentication failure".
A bit stuck, I read the config file nhttpd.conf and the Nostromo's manual again. Oh! There is something I forgot, it's the homedirs. This configuration allows users to access their home directory by an URL with the character "~" like that: http://10.10.10.165/~david/
Although the directory /home/david is not accessible, I can still access the directory /home/david/public_www, which is shown at the configuration homedirs_public. Browsing this directory, I see a backup file named backup-ssh-identity-files.tgz. Maybe it contains the ssh key to access the david account!
Do you remember the password hash in the file .htpasswd which we've just cracked? Using these credentials david / Nowonly4me, I can download the backup file via the browser by access this URL:
http://10.10.10.165/~david/protected-file-area/backup-ssh-identity-files.tgz
Extracting the backup file, I find the private key file which we need. However, it's encrypted by a passphrase so I use john to crack it.
Now, using the passphrase "hunter", I can ssh to the david account and own the user flag.
Own root
I think this part is straighter and easier than the user part above. Browsing the home directory of david, I find a strange file named server-stats.sh.Inside this file, there is only a command takes my notice:
Oh, a command with sudo, it's definitely where to get root! If you know GTFOBins, you may also know that journalctl will invoke the command less and inside the less window, you can spawn a shell. Here comes a trick, if your terminal's width is smaller than the output's longest line, the less window will be held and you can spawn a shell from it. Otherwise, it will return back to the terminal.
Note that you can only use exactly the command "/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service" to run with sudo privilege without a password in this box.
Finally, we just grab the root flag!
My lessons learned
- Don't overlook the configuration file and the manual!
I kept stuck with escalating privilege from www-data to david until I read the Nostromo's manual again and found out what the configurations homedirs and homedirs_public are.
So, RTFM! - Many information can be grabbed from the HackTheBox's forum!
Just use it like an OSINT hunter. I found the "resizing terminal window" technique to make the less window remain when reading others' comments on the forum.
If you have any questions, please don't hesitate to ask me on Twitter or leave a comment.
Thank you for reading!
















Comments
Post a Comment